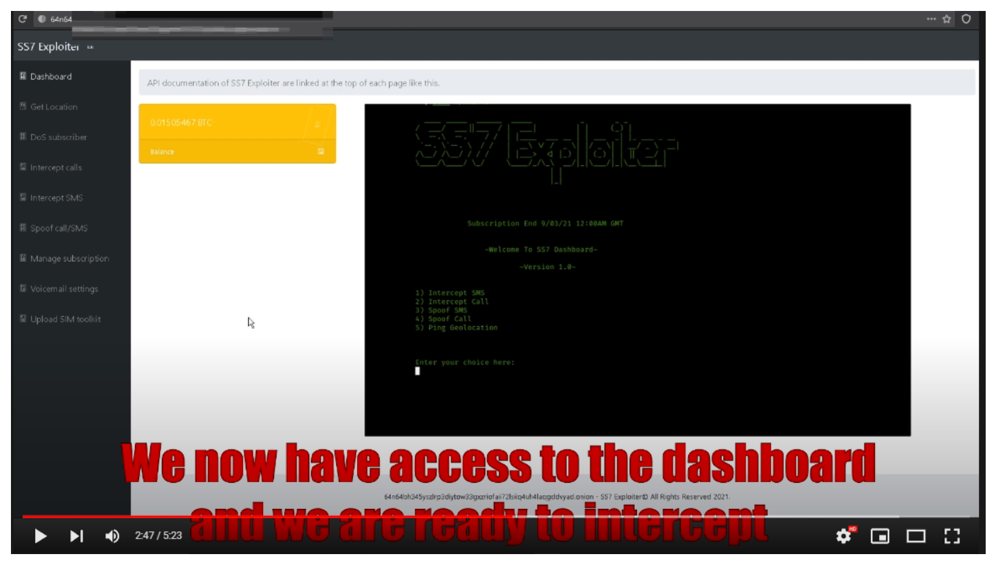
Telegram Hack using SS7 Attack | Apart from more sophisticated and advanced technologies available to Governments, Enterprises, Terrorist Groups and general hackers. This SS7 Attack... | By Blackphone SA | Facebook

The weaknesses in the part of global telecom network SS7 | Facebook, skill | Hackers with skills to exploit the SS7 network can hack your Facebook account by your phone number. The

.jpg)